Auth0
To configure Appsmith to use Auth0 as a SAML provider, follow the steps below:
Prerequisites
- A self-hosted Appsmith instance. See the installation guides for installing Appsmith.
- Before setting up Single Sign-On (SSO), ensure that you have already configured a custom domain for your instance.
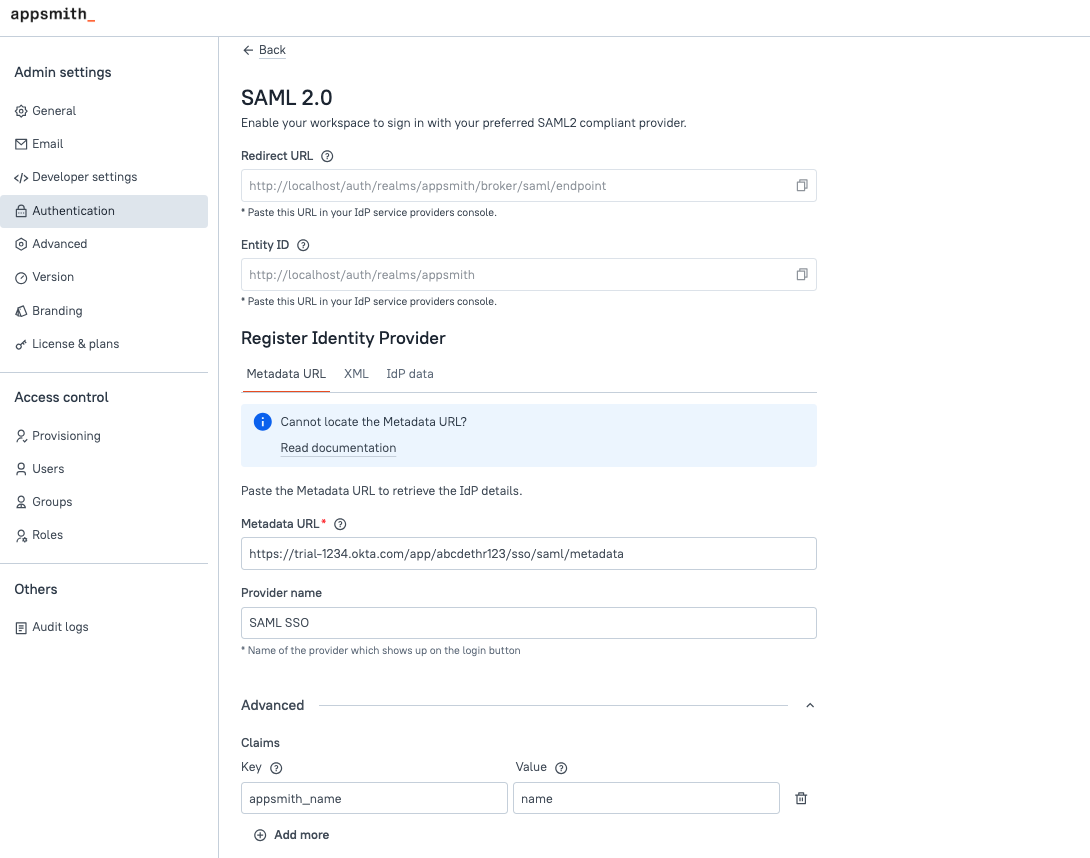
- In Appsmith, go to Admin Settings > Authentication and click Enable on SAML 2.0.
- Copy the Redirect URL from the SAML 2.0 configuration page to add it later in the Auth0 settings.
Create application on Auth0
- Log in to your Auth0 account and go to Applications > Create Application.
- In the Create application modal, select Regular Web Application and click Create.
- Once your application is created, you’re taken to the Quick Start screen. Go to the Settings tab.
- Scroll down to the Application URIs and paste the Redirect URL copied earlier in the Allowed Callback URLs field.
- Click Save Changes.
- On the Settings tab, go to Advanced Settings > Endpoints. Scroll down to the SAML section, and copy the SAML Metadata URL to add it later in the SAML configurations in Appsmith.
Register Auth0 in Appsmith
To complete the SAML configuration, you have to register the identity provider on Appsmith. Appsmith provides three options to register the identity provider as mentioned below:
- Metadata URL (recommended)
- Metadata XML
- IdP data
To register Auth0 as the identity provider on Appsmith, follow the steps below:
- If you are running Appsmith on Google Cloud Run, AWS ECS, or Azure Container Instances, make sure to configure the service before setting up SSO. For more information, see:
-
Go to the SAML 2.0 configuration page in Appsmith and navigate to Register Identity Provider section.
-
Add the copied Metadata URL in the Metadata URL field under the Register Identity Provider section.
To set up SAML using the raw Metadata XML file, follow the steps below:
- If you are running Appsmith on Google Cloud Run, AWS ECS, or Azure Container Instances, make sure to configure the service before setting up SSO. For more information, see:
-
Open the copied Metadata URL in a browser tab and copy the XML content.
-
Navigate to Appsmith and add the raw XML in the Metadata XML field under the Register Identity Provider section in the SAML 2.0 configuration page.
If you have Identity provider data like X509 Public Certificate, Email, you can choose this option to configure SAML.
- If you are running Appsmith on Google Cloud Run, AWS ECS, or Azure Container Instances, make sure to configure the service before setting up SSO. For more information, see:
-
Open the Metadata URL in a browser tab or open the Metadata XML file.
-
Add the following values from XML tags in IdP Data under the Register Identity Provider section in the Appsmith SAML 2.0 configuration page:
**IdP Data Field ** | Metadata XML Tag |
|---|---|
| Entity ID | Enter the value of the entityID attribute specified in the <EntityDescriptor> tag. |
| Single Sign-On URL | Enter the value of location attribute specified in the <SingleSignOnService> tag. |
| X509 Public Certificate | Enter the value specified in the <X509Certificate> tag. |
Enter the value specified in the <NameIDFormat> tag. |
Once you have added the details, click the SAVE & RESTART button to save the configuration and restart the instance.
If you're running Appsmith on a Kubernetes cluster with an HA configuration, after completing the setup, run the following command to ensure the new authentication settings are properly applied:
kubectl rollout restart deployment/appsmith -n
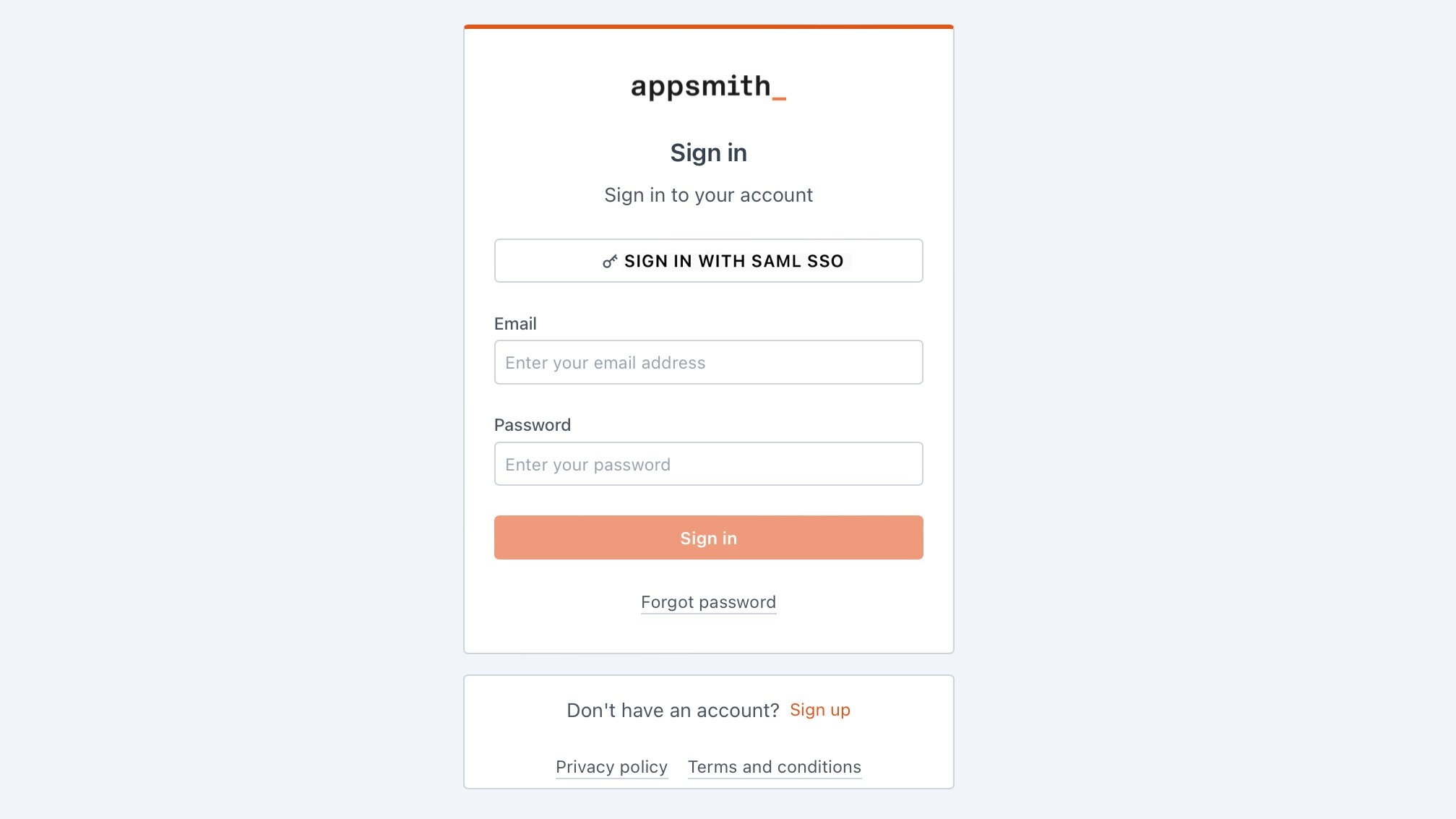
After the Appsmith instance restarts, try logging in again to your account. You'll see a login screen with the SIGN IN WITH SAML SSO button.
Troubleshooting
If you are facing issues contact the support team using the chat widget at the bottom right of this page.